Overview
Order Time advanced security features are available to give your management team full control over your company file. Access control in this day and age is more important than ever. These three features take access control to the next level.
IP Restrictions
You must be an Admin to edit the Roles for your company. Head to your Admin section, click on Roles. Click on the Edit button on the Role you wish to edit. Click on the IP Restrictions Tab.
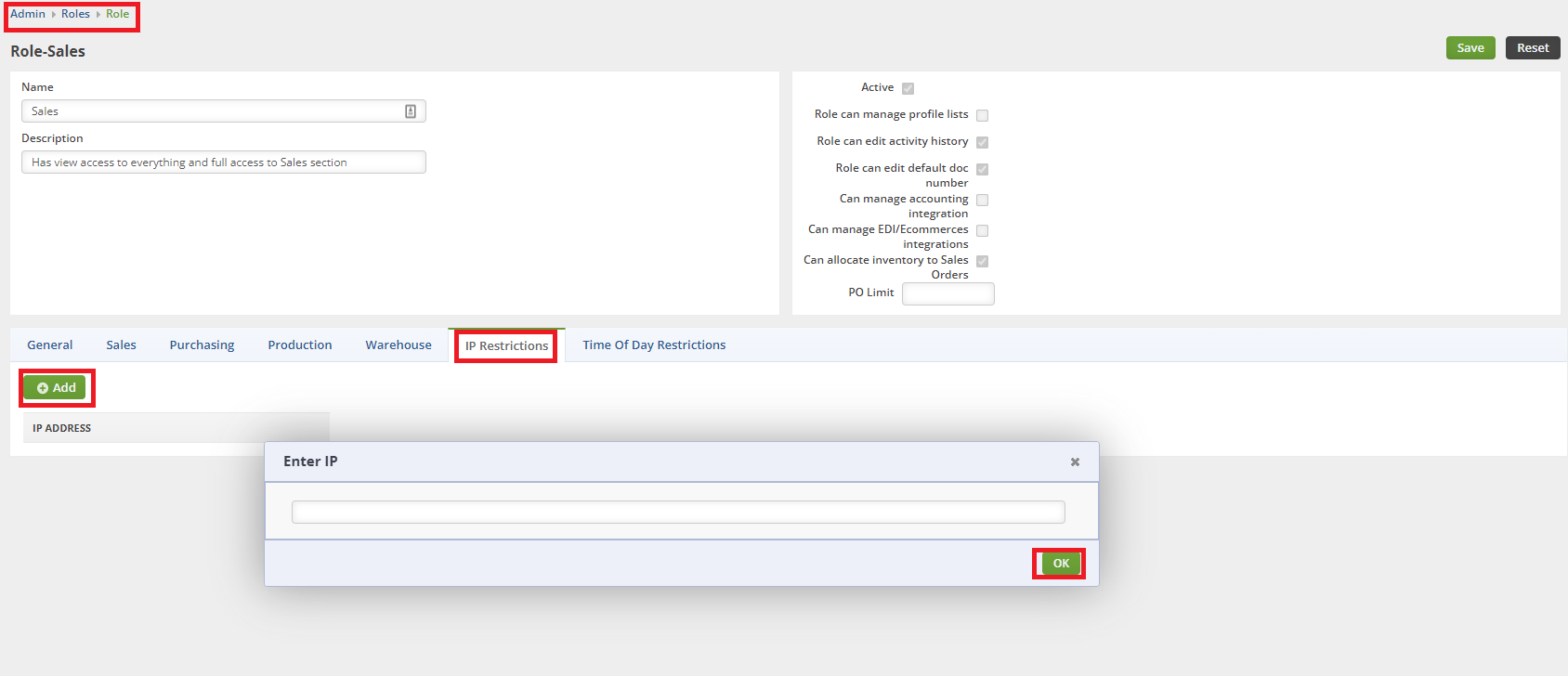
From here you can enter all the whitelisted static IP addresses you wish to allow for this Role.
- If no IP addresses are listed then all IP addresses can login as this Role.
- The restriction occurs when at least one IP address is listed.
- Make sure the IP addresses on your network block are static. Dynamic addresses could be locked out by accident!
After adding the addresses you want, click on the Save button in the top-right corner.
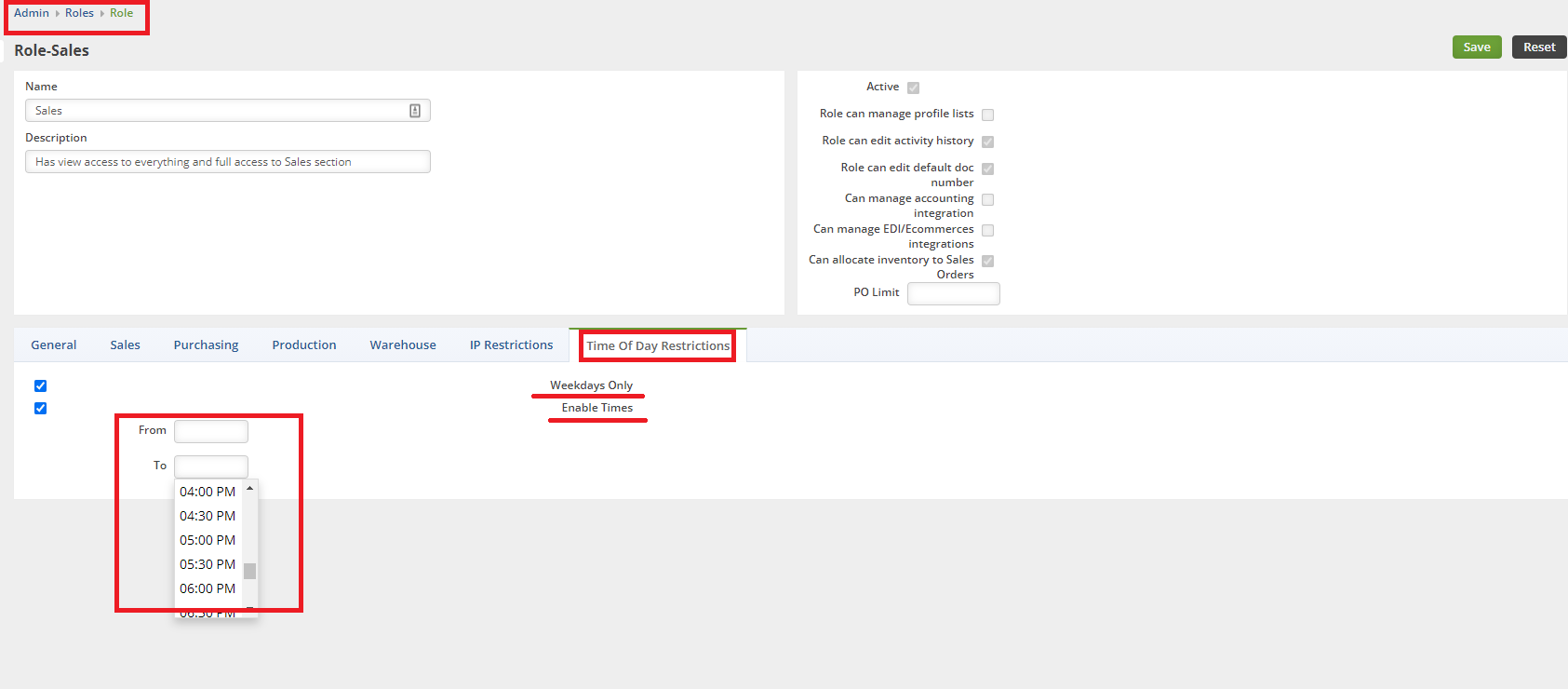
Time of Day Restrictions
You must be an Admin to edit the Roles for your company. Head to your Admin section, click on Roles. Click on the Edit button on the Role you wish to edit. Click on the Time of Day Restrictions Tab.
Weekdays Only - Restricts this Role's access to only Mon-Fri
Enable Times - Restricts this Role's access to only a particular Start Time and End Time. Access outside of the preordained shift is restricted.
Both can be enabled at once for superior control over access for particular roles.
Using both the IP Restriction and Time of Day Restriction gives your company next level access control. Be warned that this can hamper logins from home or from mobile devices if it is not implemented properly. For any questions, reach out to support@ordertime.com
Two-Factor Authentication (2FA)
In release version 1.033 we changed the two-factor authentication from emails and text messages to the Google Authenticator. This provides Order Time Inventory with top of the line security which will take us into the future of online apps.
One of the best ways to protect your account is to have an extra form of verification in place. Two-factor authentication helps keep out anyone who shouldn’t have access to your account by requiring a second step after you enter your password.
Learn more about 2FA here: Google Authenticator - New Two-Factor Authentication